Automated Attack Surface Management & Monitoring
Automated attack surface monitoring finds forgotten assets, vulnerable services, and shadow IT that slip through the cracks. Real-time DNS monitoring and subdomain enumeration with instant alerts.
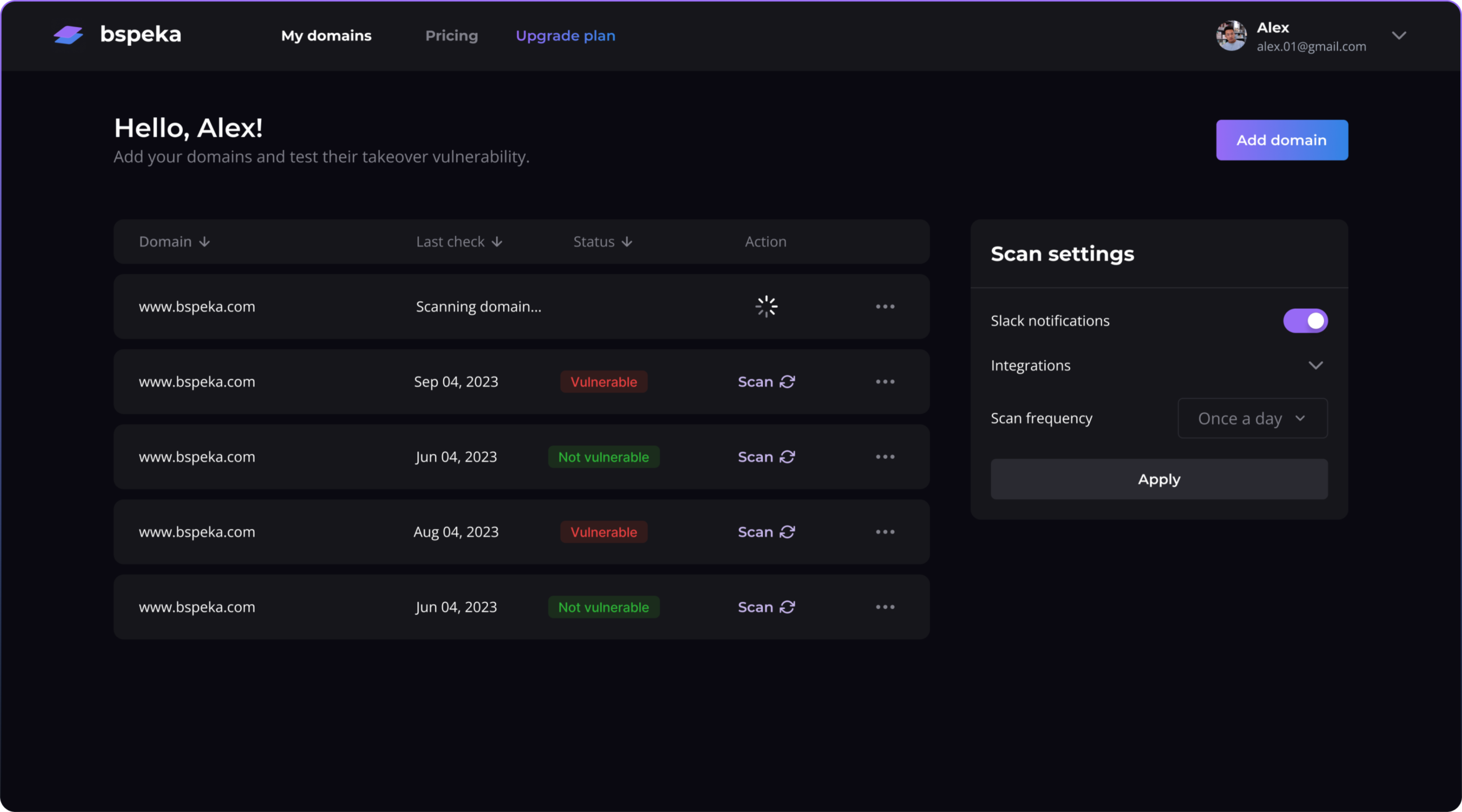
Automated attack surface monitoring finds forgotten assets, vulnerable services, and shadow IT that slip through the cracks. Real-time DNS monitoring and subdomain enumeration with instant alerts.

76% of organizations have experienced attacks due to mismanaged internet-facing assets they didn't know existed
Your attack surface is 10x larger than you think. Forgotten subdomains, orphaned DNS records, and shadow IT create blind spots that attackers exploit first.
2,300 vulnerability alerts but no way to know which assets matter. Manual tracking is error-prone and always outdated.
Traditional security tools give you snapshots, not continuous visibility. By the time you discover the misconfigured subdomain, attackers are already inside.
Production-ready in 15 minutes. No complex deployment, no security expertise required.
Add your root domain, confirm with a TXT record, and we immediately discover all subdomains through DNS enumeration, certificate transparency logs, and direct integration with AWS Route 53, Cloudflare, Google Cloud DNS, and Azure DNS.
24/7 scanning for DNS security issues, open ports, weak SSL/TLS configurations, subdomain takeover vulnerabilities, and service misconfigurations. Stop operating with snapshots—get real-time visibility.
No more drowning in 2,300 alerts. Get prioritized notifications via email, Slack, or SMS only when something actually matters. Know immediately when new vulnerabilities appear or configurations change.
Choose the plan that fits your needs. All plans include core monitoring features.
Join security teams who eliminated their blind spots and reduced their attack surface by an average of 40% in the first 30 days.
Start Monitoring Free for 14 Days